SELinux
Security Enhanced Linux is an implementation of MAC, as opposed to mechanisms based on file permissions, provides greater security in access and interactions between objects (devices, files) and subjects (users, processes, communications and actions) of the system. In addition, this access control system is “transparent” to the system user and its configuration depends on an administrator with maximum privilege in the system.

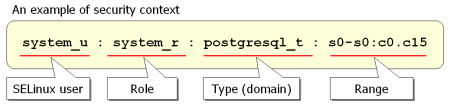
It is based on “security contexts”, assigning tags to every element under supervision and a policy defining which access and which operations are allowed. The rules established by the SELinux policy will be applied on a mandatory basis on the contexts, over and above the file permissions (read, write, execute), typical of a discretionary access control ([DAC]).
There are two fundamental terms to understand SELinux: tags and types of restrictions. With SELinux every file, user, port, process, etc. has tags that will characterize the permissions and actions it is allowed to perform and make up what is called a SELinux security context. The restrictions are determined by the rules established in the policy.
Policies:
SELinux incorporates two types of policies:
- Targeted policy: Where only a number of selected system processes are under SELinux control. (apache, dns, proxy squid, snmp y syslog). This is the default policy and provides a fairly effective and relatively easy-to-administer control. All other daemons or processes are outside the SELinux security context and to which standard Linux security applies.
- Multilevel/Multicategory Policy (MLS/MCS): This is an advanced SELinux application of a complexity and scope that is beyond the scope of this article. It is used when you want to provide strict control, for example, in security-critical organizations.
Tags:
SELinux tags follow the following format:
user:role:type:level(sensitivity:category)
- user: identifies the selinux user, a different concept than the Linux user.
- role: is the part of the role-based model ([RBAC]) also used by SELinux.
- type: defines the type of restriction. In the case of a process, it is called a domain and in the case of a file it is called a type. The SELinux policy rules determine how types can access each other, domains with types, or access between domains.
- level: is used with advanced MLS/MCS policies. These are extensions that allow even more precise control through additional tagging with two entities: sensitivity and category. The sensitivity tag is hierarchical, so a process at a certain level has read access to lower levels but can only write at the same or higher level. The category tag is a non-hierarchical attribute. With this type of policy, more granular and precise rules can be defined, although the complexity increases.
Operation:
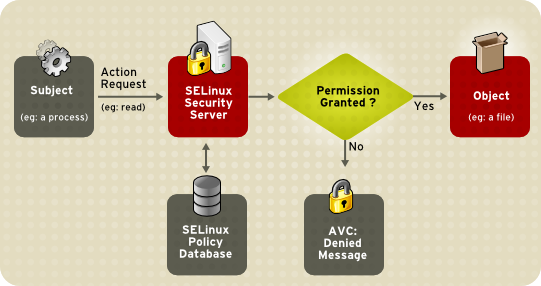
The rules defined in the SELinux policy are cached by the system kernel in AVC (Access Vector Cache) vectors containing the permissions of each object and subject under control. When an operation or access is to be executed, the kernel checks the AVC cache allowing or blocking the action accordingly.
For more information you can see the official Red Hat Manual.
Mode of Execution:
SELinux is installed by default in distributions such as CentOS, Fedora or RedHat and can operate in three different modes:
- Enforcing: SELinux enforces its policies and takes the established actions if any violation of the policy occurs.
- Permissive: SELinux enforces policies but does not take action, it only logs and alerts the administrator that a rule has been violated.
- Disabled: SELinux is disabled.
We can check the status and the running mode of this tool in the file /etc/selinux/config or otherwise run it in the console:
sudo sestatus
To obtain the execution mode in SELinux we execute:
sudo getenforce
To change the execution mode of SELinux:
sudo setenforce <permissive/enforcing/disabled>