Access Control Policies
An access control policy specifies the access rights that regulate whether an access request made should be allowed or not. Access requests are made by what is called a principal, which can be: a user (human), a subject (a process running on behalf of a user) and an object (a data or a resource).
We can classify access control policies into different types, each with its advantages and disadvantages:

Discretionary Access Control (DAC)
Discretionary access control is a method of restricting access to objects based on the identity of the subjects that intend to operate or access them. The most representative example is the permission mechanism established by the owner (user/group) of the subject. Thus, it is the owner of the object himself who determines which users and with which privileges access his objects. This access mechanism is present in most operating systems. In this type of access control it is common to use attributes (read, write, execute, etc.) to mark the permissions applied to the object.
In the specific case of UNIX/Linux systems, system objects (files, directories, etc.) have read (r), write (w), and execute (x) attributes. These permissions are assigned by the owner user (user), for the group (group) and for third parties (others, non-owner and non-group users). With the ls -l command we can visualize the basic DAC permissions.
ls -l
-rwxrw-r-- 1 user group 0 date file
There are other properties such as ACLs (access list control) and other special permissions such as sticky bit, or setuid, setgid (Linux) permissions that add more options to DAC access control.
Mandatory Access Control (MAC)
In enterprise environments, data protection is important, and having a security strategy in place is a prerequisite to protect customer data and internal information from unauthorized access and unwanted use.
To solve this problem, there are several models to implement and maintain this access control, one of them is the Mandatory Access Control (MAC) is a model for controlling user access to resources (objects, files, systems, processes, ports, etc.) based on access rights established by a central authority. Mandatory rules are established to protect access to resources by unauthorized users.
However, defining and assigning access authorizations to each user or computer can be a complex task even for companies; it is usually up to the central administration of the company to assign these permissions. This is usually done by a person with knowledge of the employees tasks, which ensures that all employees can carry out their activities without restrictions and are not restricted because they do not have a specific authorization.
In Linux there are tools capable of helping us with the management of these authorizations, we can find SELinux (Security Enhanced Linux) used in distributions such as CentOS or Ret Hat, and also AppArmor used in Debian systems.

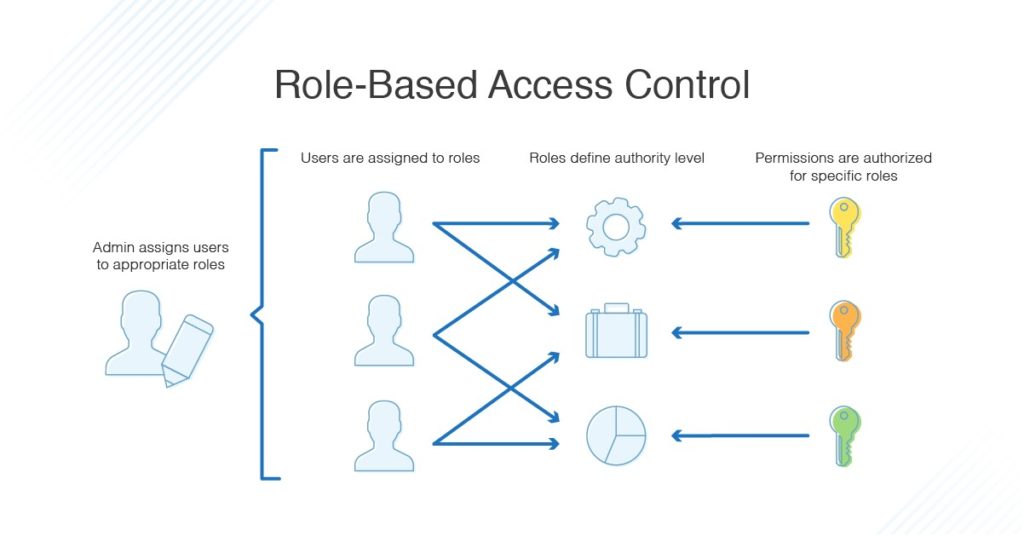
Role Based Access Control
Discretionary access control does not provide sufficient granularity to allow for more defined and structured segmentation in a complex system with a multitude of users and roles. In this case, a role-based mechanism provides greater versatility. Role-based access control consists of defining profiles (roles) to which a series of characteristics are attributed that apply to the permissions and actions they can carry out, including control over other profiles. It is, in a way, a hierarchical system of classes.
This is widely used in organizations with a large number of users and where different work groups or departments with differentiated functions are integrated, such as systems department, development department, commercial department, general services, etc. With this mechanism, access to objects and tasks is segmented and organized efficiently. Representative examples of these mechanisms are LDAP, Active Directory of Microsoft Windows or FreeIPA of Fedora/Redhat. Some UNIX systems such as Solaris or AIX also implement this privilege system.
Rule Based Access Control
Although the acronyms coincide with that of role-based access control, the two should not be confused. Access to resource objects is granted or denied based on a set of rules defined by a system administrator, and cannot be changed by users. As with DAC, access properties are stored in access control lists (ACLs) associated with each resource. When a user or group attempts to access a resource, the access control list rules for that object that have been defined by the system administrator are checked. For example, these rules may allow access to the network only from certain IPs, or allow access from a specific IP unless it comes from a specific port, or restrict access to data only during business hours.